The Importance of a Secure Document Management System
In today’s digital age, the need for a secure document management system cannot be overstated. With the increasing volume of sensitive information being created and shared online, organizations must prioritize the security of their documents to protect against data breaches and unauthorized access.
A secure document management system provides a centralized platform for storing, organizing, and accessing documents while implementing robust security measures to safeguard sensitive data. By leveraging encryption, access controls, audit trails, and other security features, organizations can ensure that their documents are protected from cyber threats and comply with data privacy regulations.
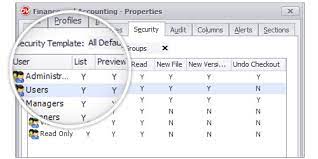
One of the key benefits of a secure document management system is the ability to control access to documents based on user roles and permissions. This helps prevent unauthorized users from viewing or editing sensitive information, reducing the risk of data leaks and insider threats.
Furthermore, secure document management systems offer version control capabilities that track changes made to documents over time. This not only helps maintain data integrity but also enables organizations to revert to previous versions in case of errors or malicious alterations.
Another important aspect of secure document management is secure sharing. With features such as password protection, expiration dates, and encrypted links, organizations can securely share documents with external parties while maintaining control over who can access them.
In conclusion, investing in a secure document management system is essential for protecting sensitive information, ensuring compliance with regulations, and mitigating cybersecurity risks. By implementing robust security measures and best practices, organizations can safeguard their documents and maintain trust with stakeholders in an increasingly digital world.
Five Key Advantages of a Secure Document Management System: Encryption, Compliance, Breach Prevention, Organizational Efficiency, and Safe Collaboration
- Enhanced data security through encryption and access controls
- Improved compliance with data privacy regulations
- Reduced risk of data breaches and unauthorized access
- Efficient document organization and retrieval for increased productivity
- Secure sharing capabilities for collaboration with external parties
Seven Drawbacks of Secure Document Management Systems: Costs, Complexity, and Challenges
- Initial implementation costs can be high for some organizations.
- Complex security features may require training for users to fully utilize.
- Integration with existing systems and workflows may pose challenges.
- Maintenance and updates of security protocols can be time-consuming.
- Potential risk of data loss if encryption keys are lost or compromised.
- Over-reliance on technology may lead to complacency in following security best practices.
- Intricate access controls could result in user frustration and hinder productivity.
Enhanced data security through encryption and access controls
Enhanced data security through encryption and access controls is a critical advantage of a secure document management system. By encrypting sensitive documents and implementing access controls based on user roles and permissions, organizations can significantly reduce the risk of data breaches and unauthorized access. Encryption ensures that even if unauthorized users gain access to the documents, they cannot decipher the content without the encryption key. Access controls allow organizations to restrict document access to authorized personnel only, preventing internal and external threats from compromising sensitive information. This pro not only enhances data security but also instills confidence in stakeholders regarding the protection of valuable data assets.
Improved compliance with data privacy regulations
A significant advantage of implementing a secure document management system is the improvement in compliance with data privacy regulations. By utilizing encryption, access controls, and audit trails, organizations can ensure that sensitive information is protected according to legal requirements. This not only helps in avoiding costly fines and penalties but also enhances trust with customers and stakeholders by demonstrating a commitment to safeguarding their data privacy. With a secure document management system in place, organizations can confidently navigate the complex landscape of data privacy regulations and maintain a strong reputation for upholding the highest standards of information security.
Reduced risk of data breaches and unauthorized access
A significant benefit of implementing a secure document management system is the reduced risk of data breaches and unauthorized access. By employing encryption, access controls, and other security measures, organizations can effectively protect their sensitive information from cyber threats and ensure that only authorized personnel have access to confidential documents. This proactive approach not only enhances data security but also helps maintain compliance with data privacy regulations, safeguarding the organization’s reputation and minimizing the potential financial and legal repercussions associated with data breaches.
Efficient document organization and retrieval for increased productivity
A significant advantage of a secure document management system is its ability to streamline document organization and retrieval processes, leading to increased productivity within an organization. By providing a centralized platform with advanced search functionalities, categorization options, and version control features, users can easily locate and access the documents they need in a timely manner. This efficiency not only saves valuable time that would otherwise be spent searching for files but also enhances collaboration among team members by ensuring everyone has access to the most up-to-date information. Ultimately, efficient document organization and retrieval facilitated by a secure system contribute to improved workflow efficiency and overall productivity.
Secure sharing capabilities for collaboration with external parties
One of the key advantages of a secure document management system is its secure sharing capabilities, which enable seamless collaboration with external parties while maintaining data integrity and confidentiality. By implementing features such as password protection, encrypted links, and access controls, organizations can securely share sensitive documents with partners, clients, and vendors without compromising data security. This not only streamlines collaboration processes but also ensures that confidential information remains protected throughout the sharing process.
Initial implementation costs can be high for some organizations.
One significant drawback of implementing a secure document management system is the potentially high initial costs that some organizations may face. Setting up a robust security infrastructure, acquiring necessary software licenses, conducting employee training, and customizing the system to meet specific organizational needs can all contribute to a substantial upfront investment. For smaller businesses or those with limited budgets, these initial costs may pose a financial challenge and require careful consideration of the long-term benefits versus immediate expenses. Despite the cost barrier, it is important for organizations to weigh the value of enhanced document security and regulatory compliance that a secure document management system can provide in the face of potential data breaches and legal repercussions.
Complex security features may require training for users to fully utilize.
One drawback of secure document management systems is that the complex security features they offer may necessitate training for users to fully understand and utilize them effectively. With encryption, access controls, audit trails, and other advanced security measures in place, users may require guidance on how to navigate and leverage these features to ensure the protection of sensitive information. This additional training can pose a challenge for organizations in terms of time and resources but is crucial in empowering users to actively participate in maintaining the security of documents within the system.
Integration with existing systems and workflows may pose challenges.
One significant drawback of a secure document management system is the potential challenges that arise when integrating it with existing systems and workflows. Organizations may face compatibility issues, data migration complexities, and disruptions to established processes when implementing a new document management solution. The need to ensure seamless integration while maintaining data integrity and workflow efficiency can be a time-consuming and resource-intensive task, requiring careful planning and coordination across different departments. Failure to address these integration challenges effectively can lead to operational inefficiencies and resistance from users accustomed to existing systems, highlighting the importance of thorough evaluation and strategic implementation strategies when adopting a secure document management system.
Maintenance and updates of security protocols can be time-consuming.
One notable drawback of a secure document management system is that the maintenance and updates of security protocols can be time-consuming. Ensuring that the system remains resilient against evolving cyber threats requires regular monitoring, patching vulnerabilities, and implementing new security measures. This ongoing maintenance process can demand significant time and resources from IT teams, potentially causing delays in other essential tasks and projects. Balancing the need for robust security with operational efficiency becomes a challenge when addressing the continuous upkeep of security protocols in a secure document management system.
Potential risk of data loss if encryption keys are lost or compromised.
One significant con of a secure document management system is the potential risk of data loss if encryption keys are lost or compromised. Encryption keys play a crucial role in securing sensitive information within the system, but if these keys are misplaced, deleted, or fall into the wrong hands, it can result in the permanent loss of access to encrypted data. Organizations must carefully manage and protect their encryption keys to prevent such scenarios, as recovering lost keys or mitigating the impact of compromised keys can be a complex and challenging process that may lead to irreversible data loss.
Over-reliance on technology may lead to complacency in following security best practices.
Over-reliance on technology within a secure document management system may inadvertently breed complacency in adhering to essential security best practices. While advanced security features and encryption tools can provide a strong defense against cyber threats, solely relying on these technological safeguards can create a false sense of security among users and organizations. This complacency may lead to overlooking critical security protocols, such as regular data backups, employee training on cybersecurity awareness, and timely software updates, leaving vulnerabilities that could be exploited by malicious actors. It is crucial for organizations to strike a balance between leveraging technology for security enhancement and maintaining a proactive approach to consistently following established security best practices to effectively mitigate risks in document management systems.
Intricate access controls could result in user frustration and hinder productivity.
One potential drawback of a secure document management system is that intricate access controls may lead to user frustration and hinder productivity. When users are faced with complex permission settings and authentication processes, it can become challenging for them to quickly access the documents they need, leading to delays in workflows and decreased efficiency. Moreover, constantly having to navigate through layers of security measures can create a sense of frustration among users, potentially causing resistance to using the system effectively. Striking a balance between security and usability is crucial to ensure that the document management system enhances productivity without compromising on data protection.
